Warning: New Malware Attack Targets WordPress Sites through Core-Stab Plugin

The malware
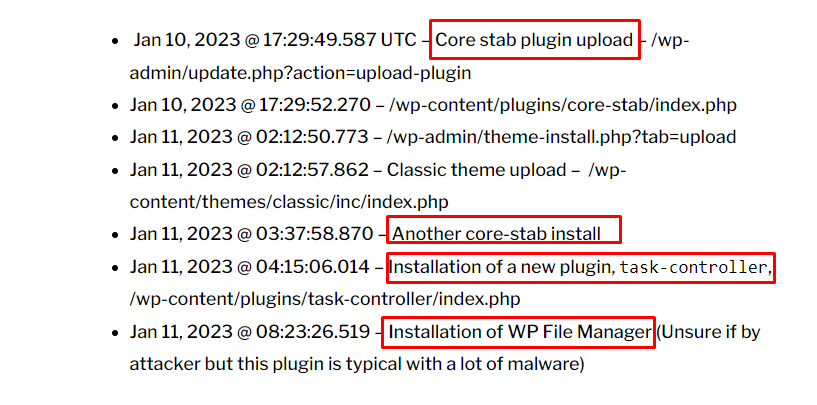
Joshua Goode, who works on WordPress.com and Jetpack.com, has looked into the malware attack on several WordPress websites. Unfortunately, this method is also used to attack Traveler’s website. This investigation found that the attack began when a plugin called “core-stab” was uploaded to the admin area of the website. The attackers then added more things, like a theme and another file of the core-stab plugin. They may have also installed WP File Manager and a new plugin called “task-controller.”
In Jetpack’s article, Joshua Goode said that the chain starts with installing the core-stab plugin, which is then followed by other things. One of the review sites was attacked by malware, as shown in the timeline below.
How to prevent this Malware Attack Targets WordPress Sites?
If you find the core-stab plugin installed on your site, the first thing you should do is REMOVE IT and then follow these next steps. There are several steps you can take to help prevent a malware attack like the one described in the article:
1.Keep the WordPress software you’re using up to date: Check your theme for files that were added or changed that you didn’t add or change. Reinstall the core files for WordPress. Make sure that WordPress, all of your plugins, and all of your themes are all running the latest versions. Outdated software can have security holes that hackers can use to put malware on your site.
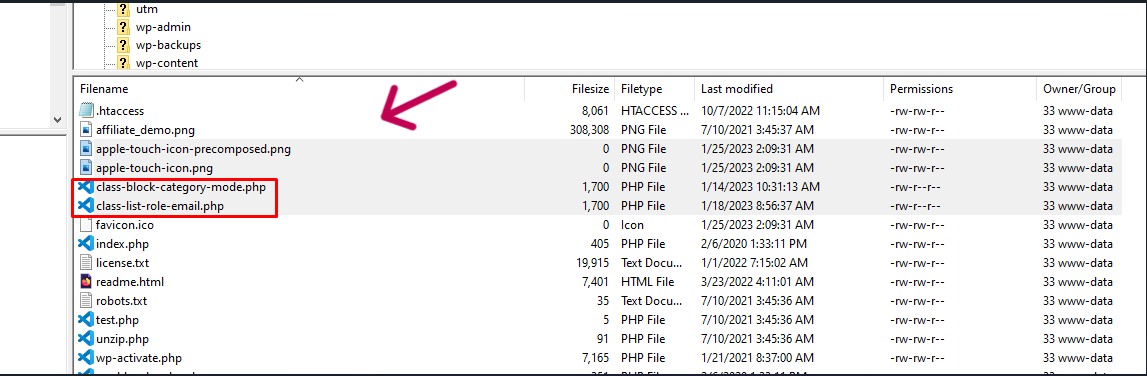
Next, if you find any files on your site that are shown in the images below, please delete them.
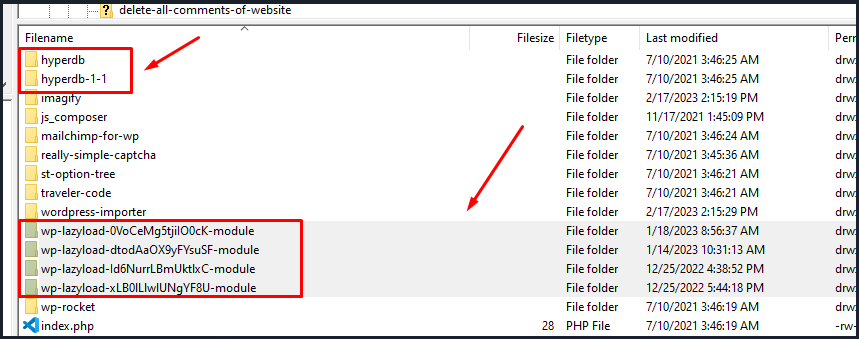
2.Change all the passwords for admin users and make sure you’re using multi-factor authentication. Use strong passwords that are at least 12 characters long and have a mix of uppercase and lowercase letters, numbers, and special characters. Also, use a different password for each site you visit, and change it often.
3.Limit who can get into the admin area. Look at all the WordPress users and get rid of the ones you don’t know (especially the admin ones). Only let trusted users into the admin area, and make sure to take access away from anyone who no longer needs it.
4.Use a security plugin to add an extra layer of security to your site, you might want to use a security plugin like Wordfence, Jetpack, CleanTalk, or Sucuri. These plugins can help find and stop attacks from malware and other security risks.
5.When you install new plugins and themes, be careful: Look for themes and plugins that aren’t being used or that you don’t know anything about. Install plugins and themes only from trusted sources, and read reviews and ratings before you install them.
6.Scan your site often for security flaws: Use a security scanning tool like Sucuri Site Check to check your website regularly for security holes and other problems.
How to Clean a Hacked Website?
Once you know where malware is on your website, the next step is to REMOVE IT and get your website back to how it was before. Fixing infected files can take a long time, especially if there are a lot of them. If you have a clean backup of your website, you should try to restore it first. This can fix your site faster and save you time. By comparing the two versions, you can see which files have been changed and need to be cleaned.
To manually remove malware from your website files, do the following:
- Make a backup of all WordPress files and database
- Disable all plugins
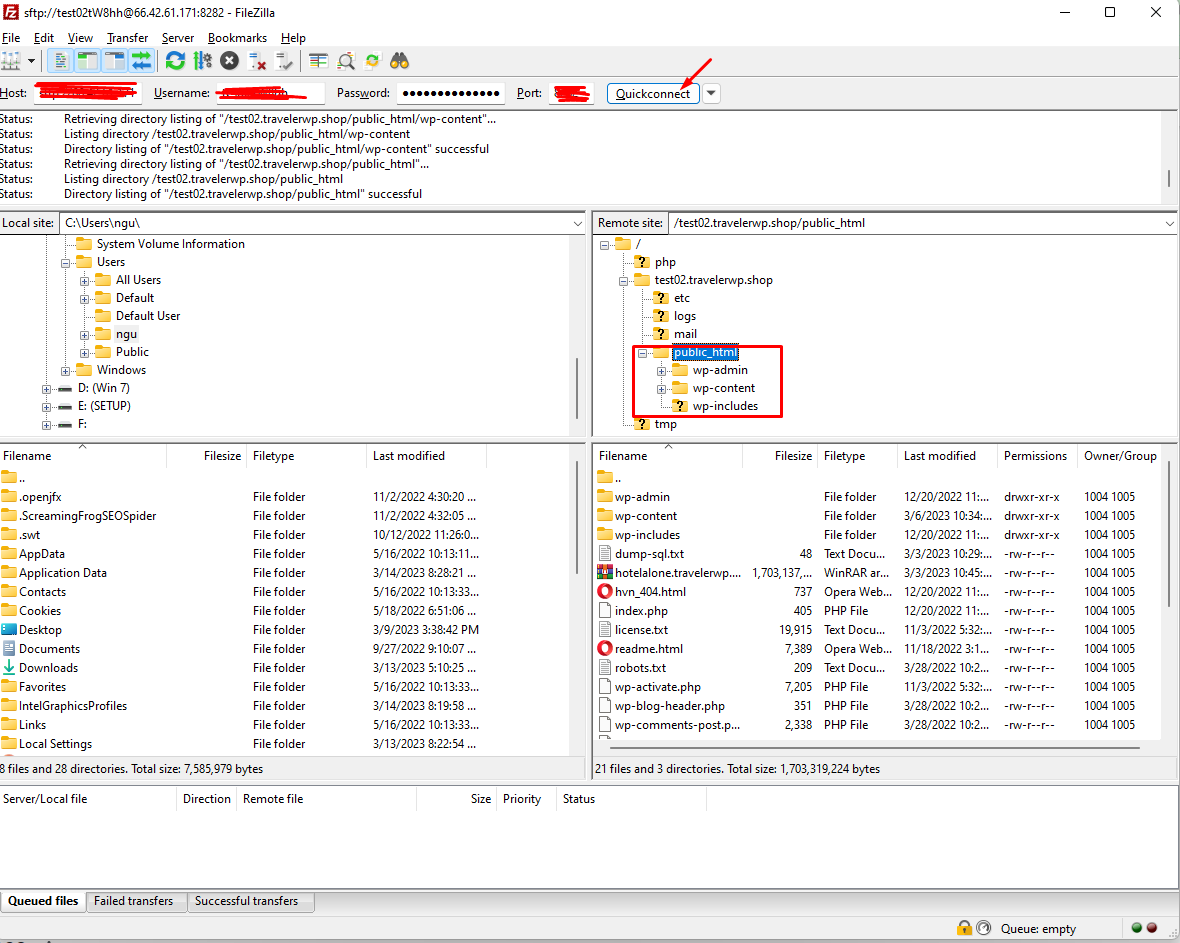
- Log into your server via SFTP, SSH, or your hosting control panel like cPanel. We recommend FileZilla which is free and easy to use when you access your back-end system
- Delete all the core files and folders of your website. And KEEP only the upload folder on wp-content folder. The “upload” folder is the location where all media files such as images, videos, and audio are stored on your website. And make a back-up folder of upload folder
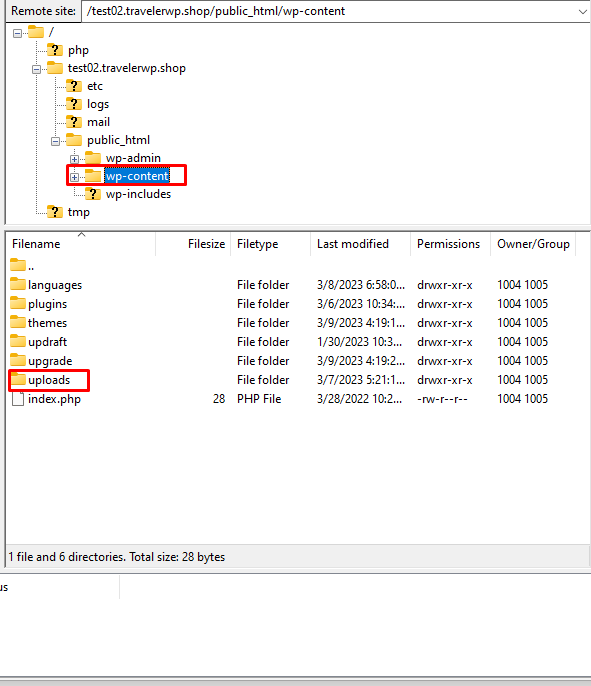
- Create a zip file of upload folder on wp-content folder. Upload it on VirusTotal to check the any suspicious files
- Upload it on VirusTotal to check the any suspicious files

- Download and unzip the WordPress installation package
- Extract the files from the compressed file. Select everything files and folders. And upload the new files using FTP. And copy upload folder to wp-content folder
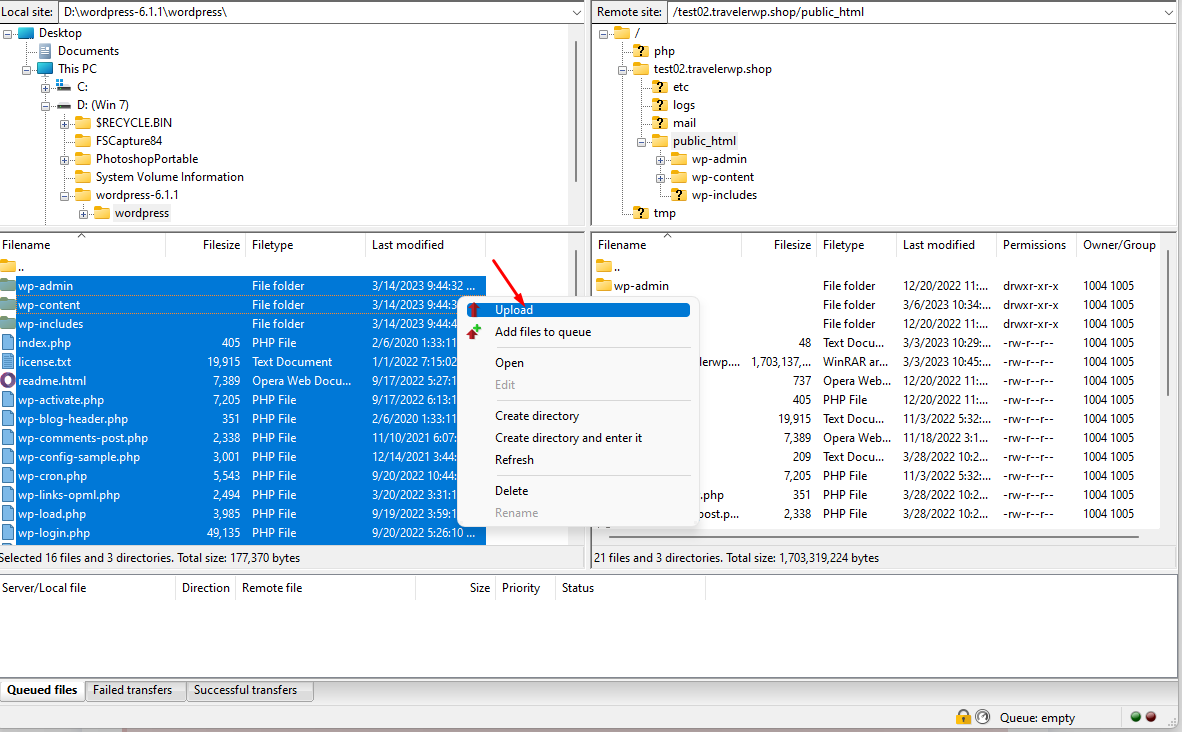
- Finally, you should re-install theme and plugin of your site.
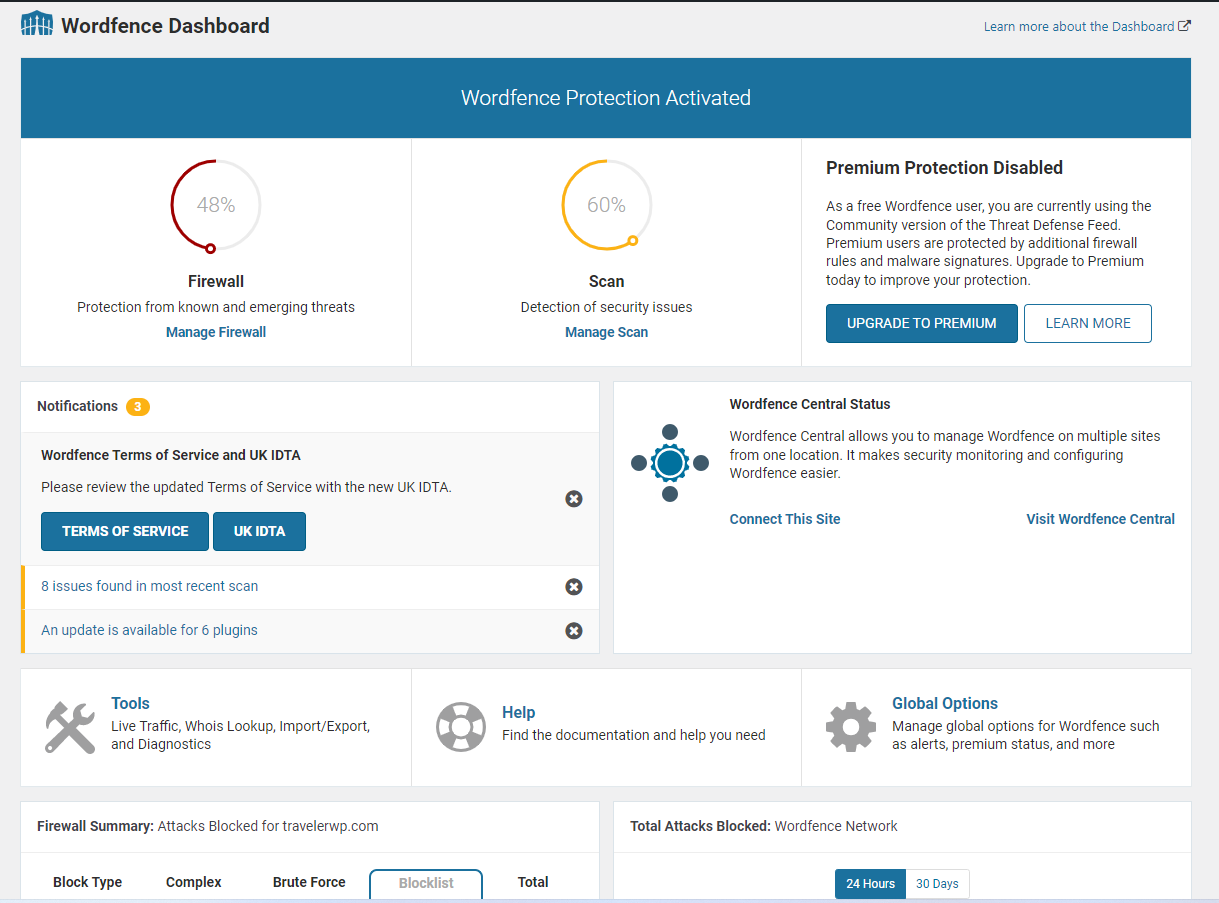
- We recommend you use Wordfence plugin which is a security plugin that helps protect your website from security threats such as malware and other online attacks. This plugin also provides features such as two-factor authentication, login security, and IP blocking
Conclusion
In conclusion, we hope that this article can help website owners and security professionals protect their sites against this type of attack.
To prevent this, the Traveler theme will be updated regularly to fix any bugs and security vulnerabilities. This will keep your site safe from malware attacks and keep it safe. Aside from that, Traveler is compatible with many popular security plugins like CleanTalk or Jetpack plugin, which can add an extra layer of security to the site.
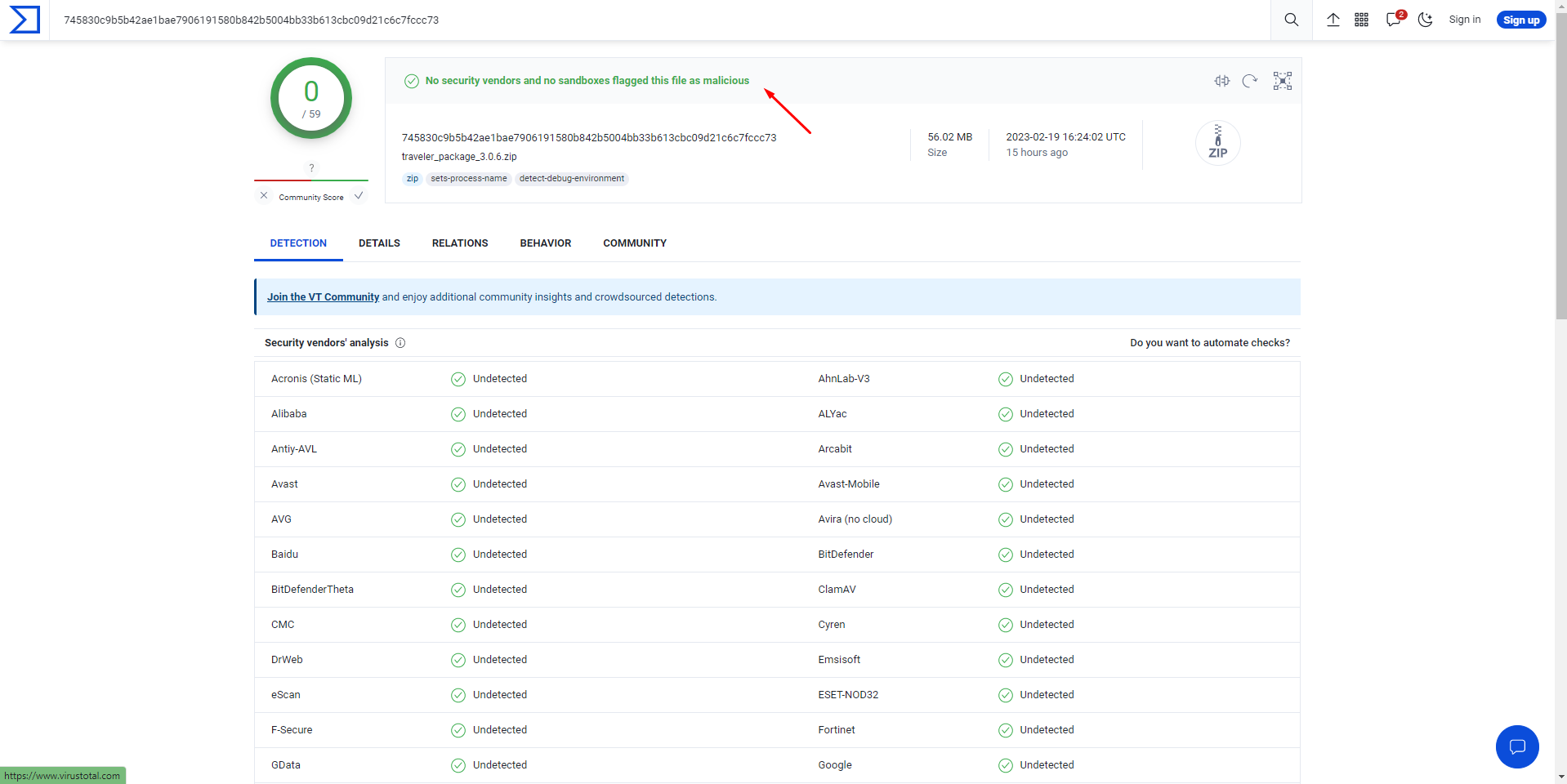
We have scanned the theme package on VirusTotal and the result is “No security vendors and no sandboxes flagged this file as malicious“. Check it out at this link
We’re so glad that you all always trust Traveler theme.